DDoS strikes again! And this time even worse
One more security incident was reported recently. This time the victim was popular code hosting site- GitHub. GitHub was hit down with massive record-breaking DDoS attack which has crossed all the past numbers of attack intensity. The attack was peaked at record 1.35 Tbps-126.9 million packets per second if we believe the numbers. This was 51000 times more than the actual request serving capacity of the site. Woah! The number describes the intensity of the attack.
Usually the botnet- a group of infected system is used to carry out the successful DDoS attacks. There is one leader/attacker which controls all the actions in the network like manipulating the IP address, change the attack payloads and other random customized activities. The notable thing in this recent attack was that there was no use of botnet reported. It was the Memcached servers which were targeted this time to escalate the DDoS attack.
How the attack was performed?
A forged request to the targeted Memcrashed server on port 11211 using a spoofed IP address that matches the victim’s IP.
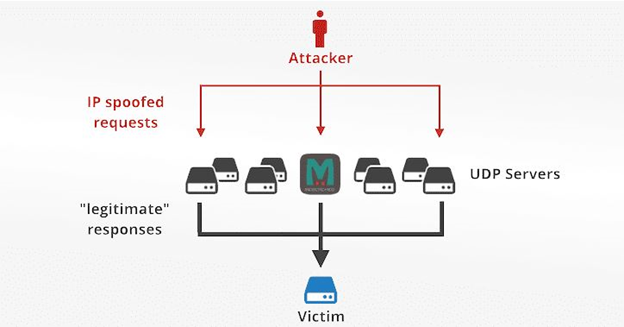
What is Memcached?
Memcached is a well-known distributed caching system which is open source and easy to deploy. It makes the use of idle RAM in severs to act as a memory cache for the frequently accessed info. It permits the object data to get stored into the memory and it runs over UDP port 11211.
Why it is used?
The motive of designing the memcached application is to achieve the performance efficiency for dynamic web application by limiting the load on the database. This not only helps to improve performance but also give a hand to achieve good scalability for the application. GitHub, Facebook, Youtube, IBM use this for the websites to name a few.
In normal scenario, displaying of information requires below actions:
- Loading the information from the database
- Data filtering (Proper data needs to be displayed in user readable form)
- Showcasing the final data
With using memcached here,
Scenario 1:
- Load the information from the cache
- If info exists, display it
Scenario 2:
- Load the information from the cache
- If info is not available in the cache, same activities are performed just like normal scenario:
-Loading the information from the database
-Data filtering (Proper data needs to be displayed in user readable form)
- STORE THIS INFO IN CACHE (Which will be helpful in the future requests)
- Display final information
According to cloud fare report, “15 bytes of request triggered 134KB of response. This is amplification factor of 10,000x! In practice we’ve seen a 15-byte request result in a 750kB response (that’s a 51,200x amplification). At peak we’ve seen 260Gbps of inbound UDP memcached traffic. This is massive for a new amplification vector. But the numbers don’t lie. It’s possible because all the reflected packets are very large”
Mitigation:
Limit the rate of traffic or close UDP traffic on Port 11211
This is the easiest way to avoid these kind of massive attacks as the exploit code for Memcached amplification attack have been released online recently.
References:



Comments
Post a Comment